Access
Control - Multiplexed System
Why use Access Control?
- Why get rid of keys?
- Access control gives you control over who gains entry to your building.
Keys also do this - so what is the difference?
- When you lose a key, you have the expense and inconvenience of replacing locks and all the
other keys, or you accept the building is no longer secure.
- With access control you simply void an individual token from the system. There is no need to
replace locks or keys.
- The security of your building is always maintained.
- Net2 is a PC based access control system, this booklet explains how it works.
Why use PC based access control?
- Central control - all doors can be controlled from one place
- Reporting - an event is generated every time a token is used to gain access
- Complete flexibility - access can be granted to users according to time and place
What are the advantages of central control?
- Full control of the system from your desk.
- Users are added and instantly have the access rights that you permit.
- Individual access rights can be altered, changes instantly update at the doors.
- Tokens voided - someone leaves without handing back their token, simply bar that user token
from the system.
- Explorer style software makes all tasks quick and easy to perform.
What does reporting give me?
- The events screen allows you to view the 'real time' events as they are happening.
- See 'who is in today' with a glance at your computer.
- You can see if unauthorised access has been attempted, either by forcing a door, or use of an
invalid token.
- Default reports are available from the software.
- Standard reports can show all events, all events in a set time frame, last known position of a user
and much more.
- Report wizard - allows you to create custom reports.
What does "complete flexibility" mean?
- Using time zones means you can allow or refuse access to different individuals or groups of
people, to different doors within set time scales.
- Why? You may for example only wish factory staff to have access to offi ces in standard office
hours. The factory staff may be set to allow access from 8am to 6pm, the offi ce door may be set
up to only allow access between 9am and 5.30pm for this group of users.
- Time zones can be created to give groups of people or individuals access at set times of day.
- Public holidays may be entered - and permissions set against these to allow or not allow access
to staff.
- Issuing cards is simplifi ed. If a department is set up with a time zone of 9am-5.30pm on the
office door, a token issued to a member of that department automatically only allows them through the door between 9am and 5.30pm.
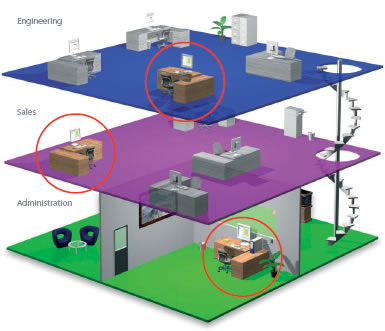
Multiple Workstations
- Provides the opportunity for more than one PC to be able to view events and control the
system.
- In the example above, three departments are able to access the system.
- Engineering - The supervisor is able to issue and void tokens, he uses the reports screen to
see who is in or out.
- Sales - The sales manager is able to issue and void tokens. He can use the report screen to check
who is in or out.
- Administration - Issues temporary one day cards to visitors. Changes access levels for different
staff and departments as needed. An alarm will generate on the events screen if unauthorised
access is attempted.
Remote sites
Can be used to control access on remote sites using dial-up via modem or TCP/IP (Local or
Wide Area Network connection LAN/WAN).
This provides many advantages:
- If premises are remote from the main offi ce and are not permanently staffed then access can be
controlled from head offi ce via the connection.
- You can bar a user from a remote site - effective immediately
- You can issue cards for a remote site - effective immediately
- Site Manager software allows control of several remote sites
- You can issue cards for a remote site in exactly the same way as at your head office
Roll Call and muster reporting
- Roll call and muster reporting is a means of checking staff in at a central point if there has been
an alarm which requires the evacuation of a building.
- A reader is located on a safe area of the site - for example a gate house
- A roll call/muster report is generated on the PC at the muster point to show who was in
the building at the time of the alarm
Staff members present their token to the reader at the muster point
The Net2 report will update to a status of "safe" against the record of the token holder
- At a glance you can check who has registered at the muster point - and who is still missing
Timesheet for time and attendance
Timesheet is used for recording simple time and attendance.
- Shows the number of hours worked by each employee
- Dedicated readers (independent of the door readers) need to be used for time and attendance
- Check at a glance, who is in, who is out, who is working out of the office, who is on holiday
- Set the number of days holiday per employee - Timesheet will show how many days remain to be taken
- Employees who work from home can log in over a network
- Timesheet information can be exported as a CSV fi le for use with payroll applications
Intruder alarm integration
- As well as controlling access into your building, Net2 can also disarm your intruder alarm if
required.
- Those users with permission to unset the alarm are fl agged using the Net2 software.
- If a system user arrives early and does not have permission to unset the alarm, they will simply
be denied access to the building. No drama, no fuss!
- On leaving the building the intruder alarm can be set by simply presenting a valid token to a
dedicated reader.
- Net2 will integrate with the majority of intruder alarm systems. Intruder alarm integration
greatly reduces the risk of false alarms and unnecessary call outs.
Site Graphics
- The ‘Site Graphics' feature allows operators to monitor events around their site at a glance.
- Site Graphics provides a visual representation of the site, complete with door locations and
real-time door status information
- Site Graphics alerts the user to door forced events or unauthorised access attempts and where they are occurring, allowing those monitoring to act swiftly to investigate the event
features we haven't mentioned
- IP camera integration - view real-time images from around your site
Integration with 3rd party readers - Biometric, hands-free and smart card
- Anti-pass back - global, logical and timed
- Link to fire alarm system - automatically unlocks any doors designated as fire doors in the
event of a fire alarm
- Triggers/Actions feature allows control of elevators, lighting, heating and much more
Features:
- The multiplexed
system is a unique
way of networking a
number of devices
through a central
control unit.
- It is ideal for
premises where
future expansion is
likely without the
necessity for heavy
investment.
- The entire
system can be
controlled and
programmed from a
central control unit
via an onboard
keypad.
- The unit is
small and
unobtrusive with an
LCD screen designed
for ease of
programming.
- Up to 1000 users
can choose between
entering keypad
pincodes, ISO/NISO
cards or tags, with
each pincode using
up to 8 digits,
giving 100 million
differs.
- The multiplexed
system has its own
range of
peripherals, i.e.
keypad, proximity
reader or expander
cards.
- Up to 30 of
these peripherals
can be connected to
the RS485 Bus.
- Control units
with or without an
integrated reader
are available.
- The Management
Software Program is
compatible with
Windows
95/98/ME/2000/NT.
- A printer can
also be connected
via the RS232 port
to print a daily
log.
There are a number of
extra features offered
by this system
including:
- Up to 3000
movements stored in
memory
- Each device can
be Access in or out
with anti-pass back
- Up to 8
schedules each with
2 time delays
- Users can be
assigned schedules,
days of the week,
devices and relays
- System can track
user movements and
hours on site
An upload/download
facility is available
through connection to a
PC or laptop via the
RS232 port. Used in
conjunction with the
Management Software
Program, this enables
several key functions,
and can be used as a
powerful investigative
tool:
- Allows full
remote programming
- Descriptions can
be assigned to
devices, schedules
and users
- Data on
movements by user
and device can be
viewed and printed
- Data on the
presence of users
and time on site can
be viewed and
printed
We have the solution to all your security needs
For a Free
consultation call 01753 880 651
E-mail: info@globaltecsecurity.com
|





